Nordic Defender, a New Paradigm of Cybersecurity
A centralized platform, a crowd-powered nature, and fully managed solutions are combined to create a seamless experience of quality expertise, cutting-edge technologies, and genuine protection.
Talk To An ExpertThe Ultimate SaaS Cybersecurity TrioAs the world’s only centralized, crowd-powered, and fully-managed MSSP, we have unified and synergized offensive, defensive, and infosec cybersecurity solutions to prevent, stop, and mitigate cyber-attack risks, preserve business growth and continuity, safeguard reputation, and maintain customer trust.

From Fragmentation to Fortification:
Unified protection through a centralized platform
- Deep insight into weaknesses and strengths
- Eagle’s view of Cybersecurity activities
- Informed decision and strategy making
- No piles of vendor assessments, supply chain, and contract management documents.
- Several security programs running in one place.
- Faster response to security issues.
- Quality and informing reports for effective management
- Industry-oriented solutions
- Customizable for SMBs and SaaS to enterprises
- Evolved solutions as your business expands
- From One-time to year-round continuous projects
- Smart budget allocation to different services
- Time-cost efficacy with managed & centralized approach
- Hourly-charged security consultancy as a service
- Bonus for starting two and more solutions
- No overhead or fixing costs charged
‣ Cyber Hygiene
Elevate Your Cyber Hygiene with Nordic DefenderStart and Elevate your cybersecurity journey with the Cyber Hygiene maturity model, designed especially for SaaS and online businesses to tackle and overcome their main cyber challenges. Take a free assessment to know your current security posture and standing and start the path to security resiliency.
Learn More‣ Next Generation Pentest
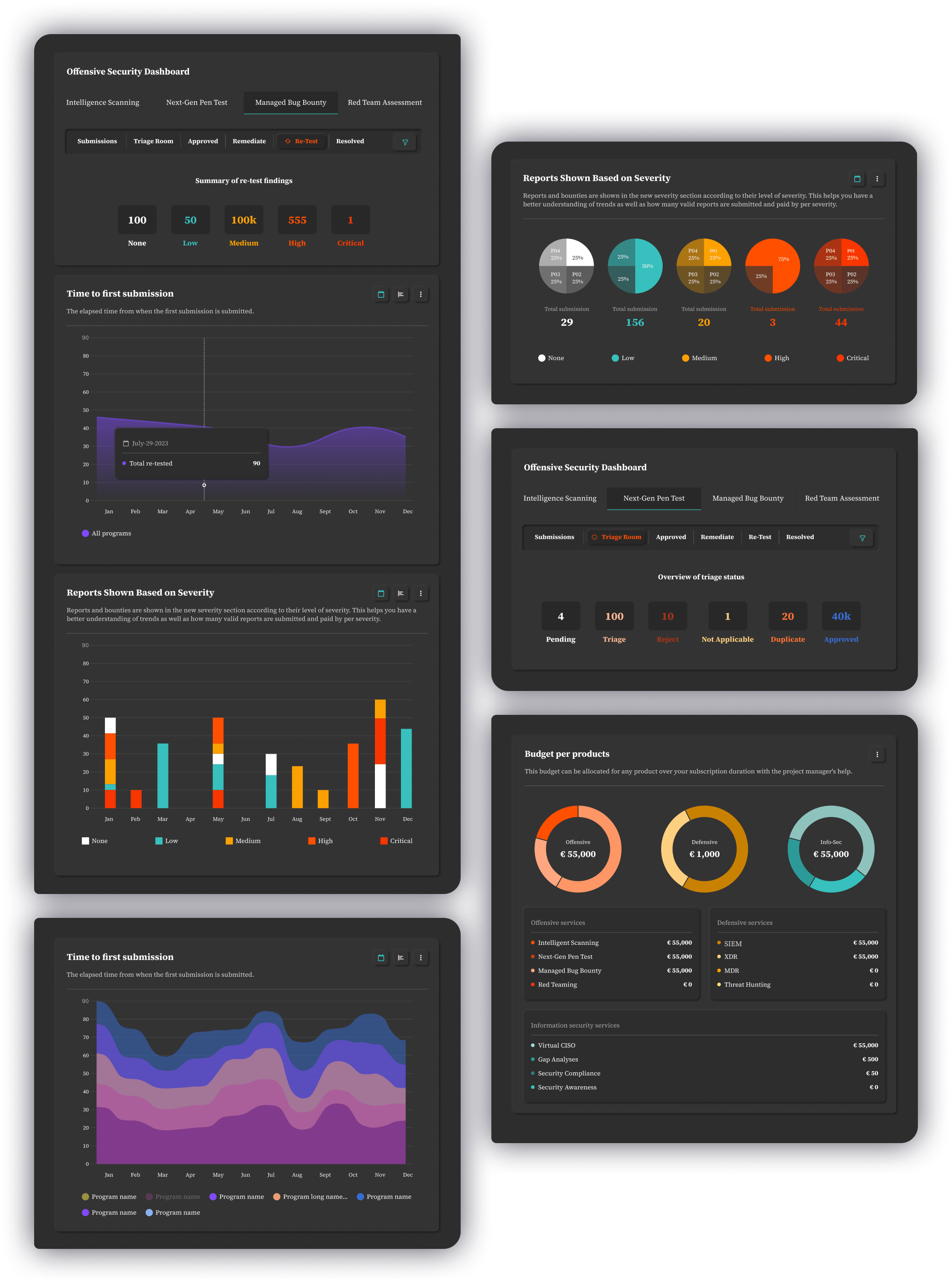
Leverage the Power of Crowd to Perform Penetration TestingDeploy highly-vetted crowd penetration testers to not only find and remediate hidden flaws, bugs, and vulnerabilities - including zero-days - but also meet your industry’s most important security framework compliance requirements. Utilize the in-depth knowledge of evolving cyber threats and cutting-edge techniques to safeguard your digital assets, providing a comprehensive and proactive defense plan that goes beyond traditional security measures.
How Does It Work?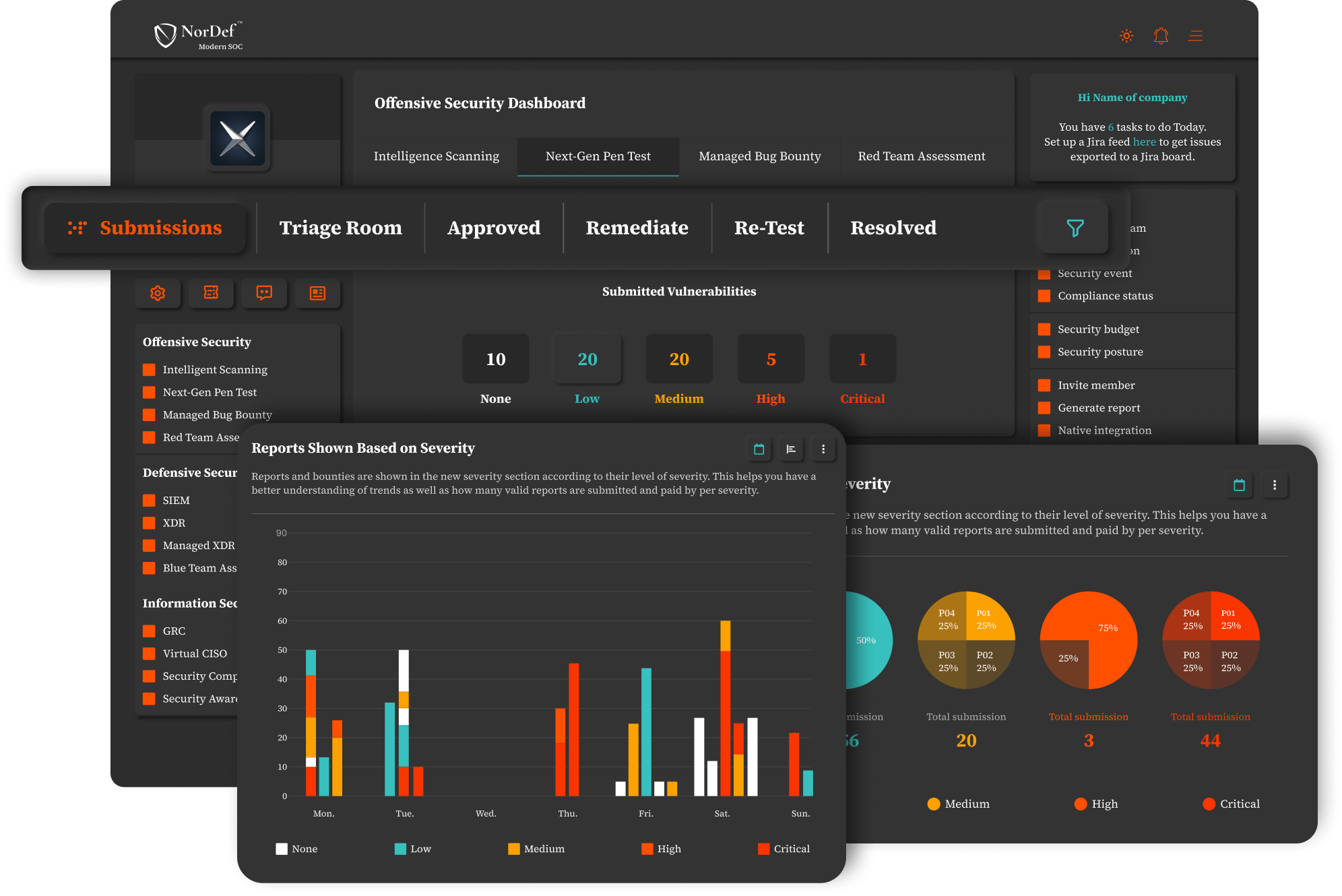
‣ Managed XDR
Managed XDR: Comprehensive TDR Operations Across Your IT LandscapeWith cutting-edge technologies for proactive defense, Managed XDR offers holistic visibility across your IT stack, detects known and unknown threats through telemetry correlation, automatically responds to them, and provides a rich detection content bank gathered by our crowd. A continuous threat hunting program, 24/7/365 monitoring, TDR efforts by our team, efficient data management, intrusion detection, and data governance operations are also other benefits you get with Managed XDR.
How Does It Work?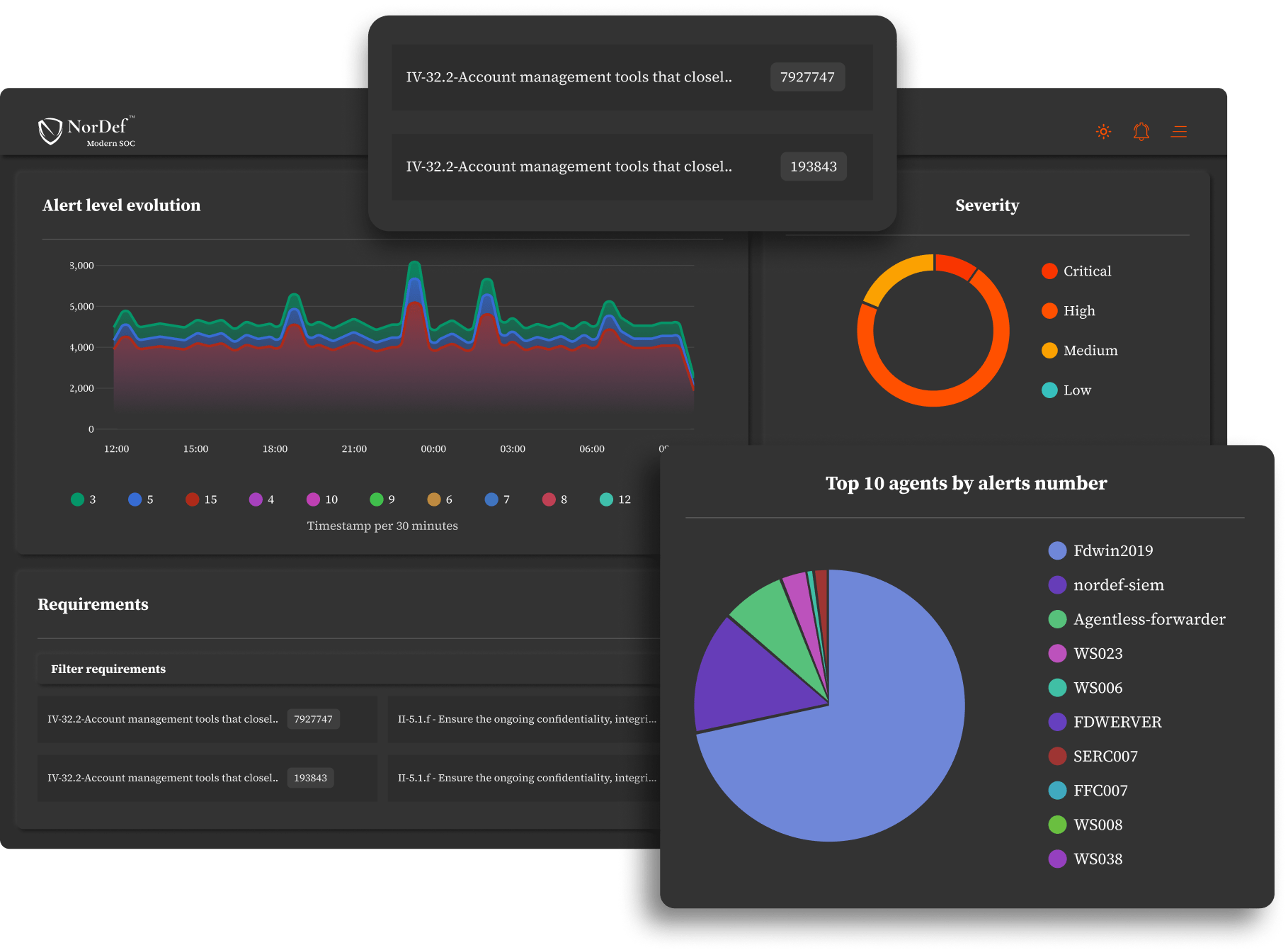
NorDef: Your External Security Department
A one-of-a-kind, single pane of glass platform to easily manage all your cybersecurity solutions centrally, with a fully-managed and crowd-powered approachAccess and Overwatch Fully-Managed ServicesPromptly access an overview of all services, active programs, total and per program statistics, budgets, results, time-invested, etc. You can also start new programs under three clusters -offensive, defensive, and infosec solutions- to make sure your safety is taken care of.
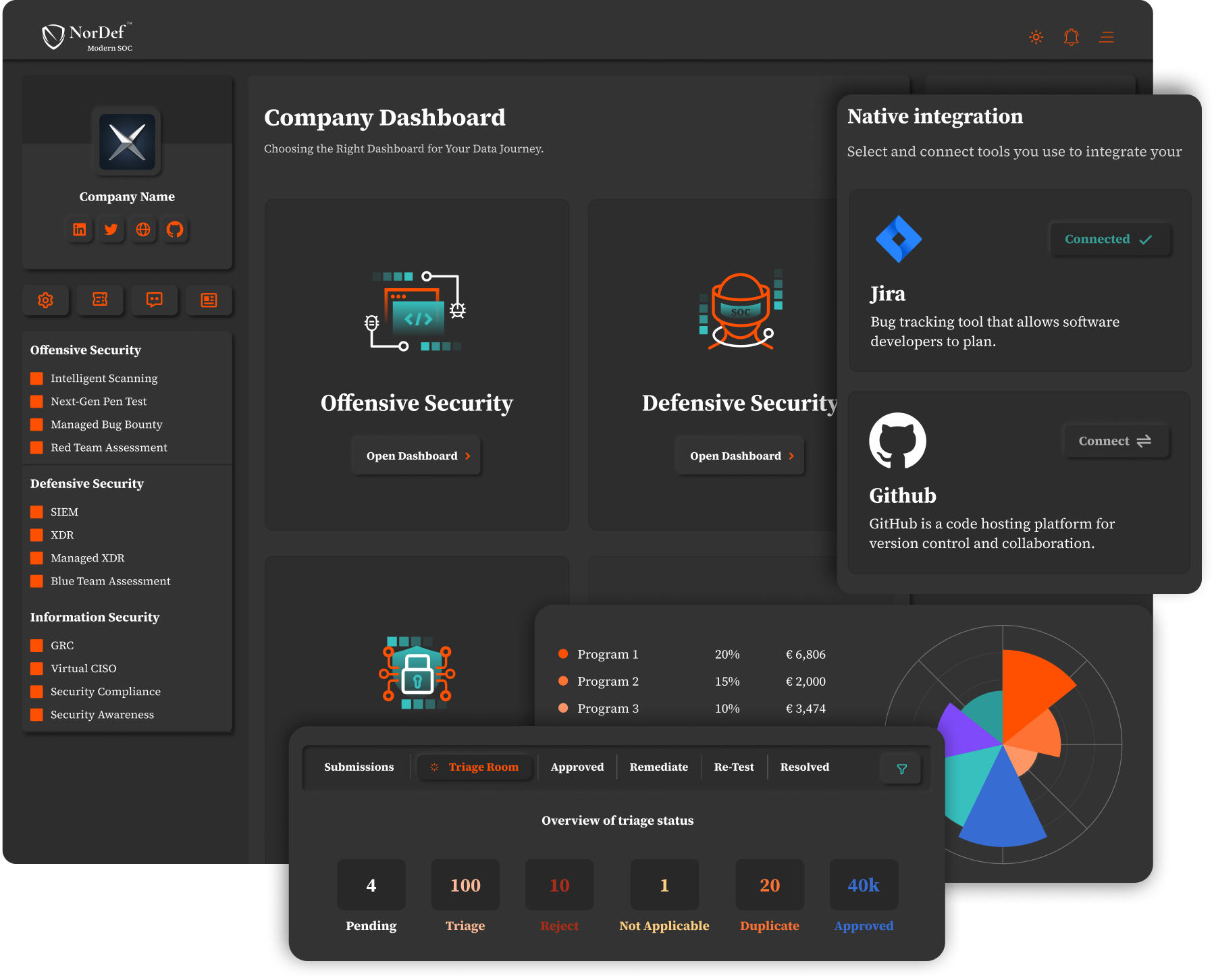
Allocate a Security BudgetA straightforward overview of your overall security budget, where it's allocated, and how much is forecasted for each program. You can also promptly increase or decrease the amount for each program.
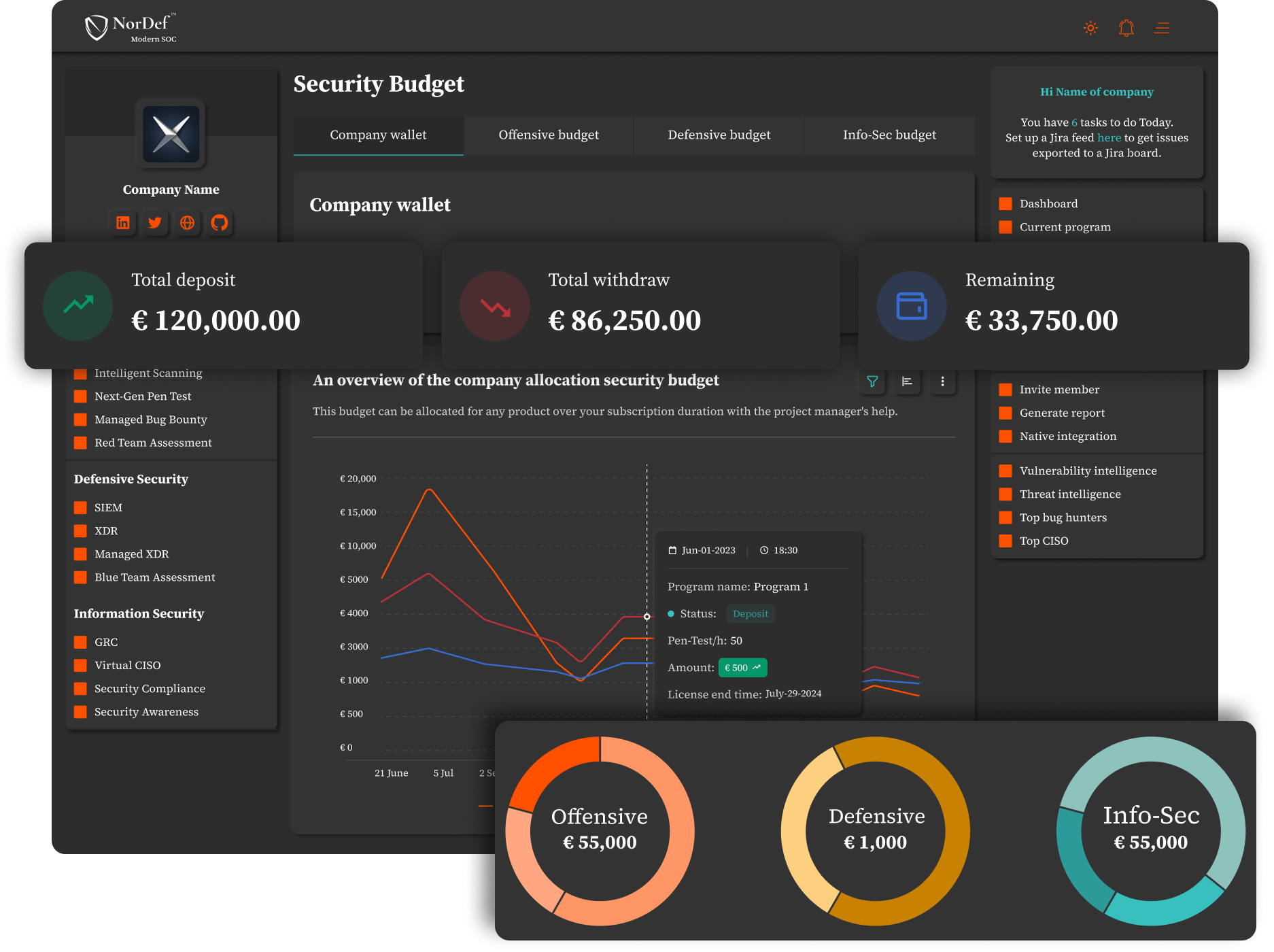
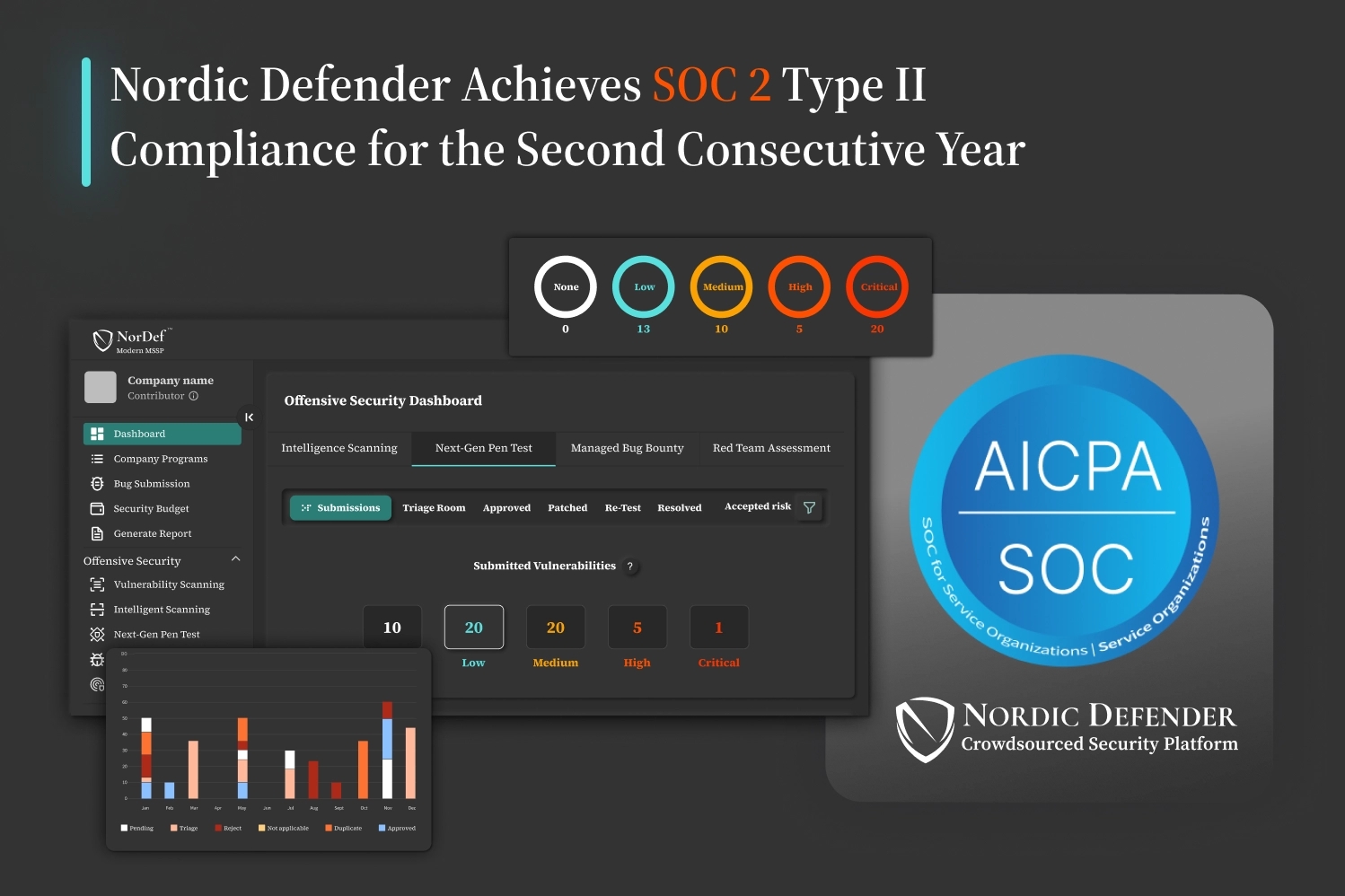
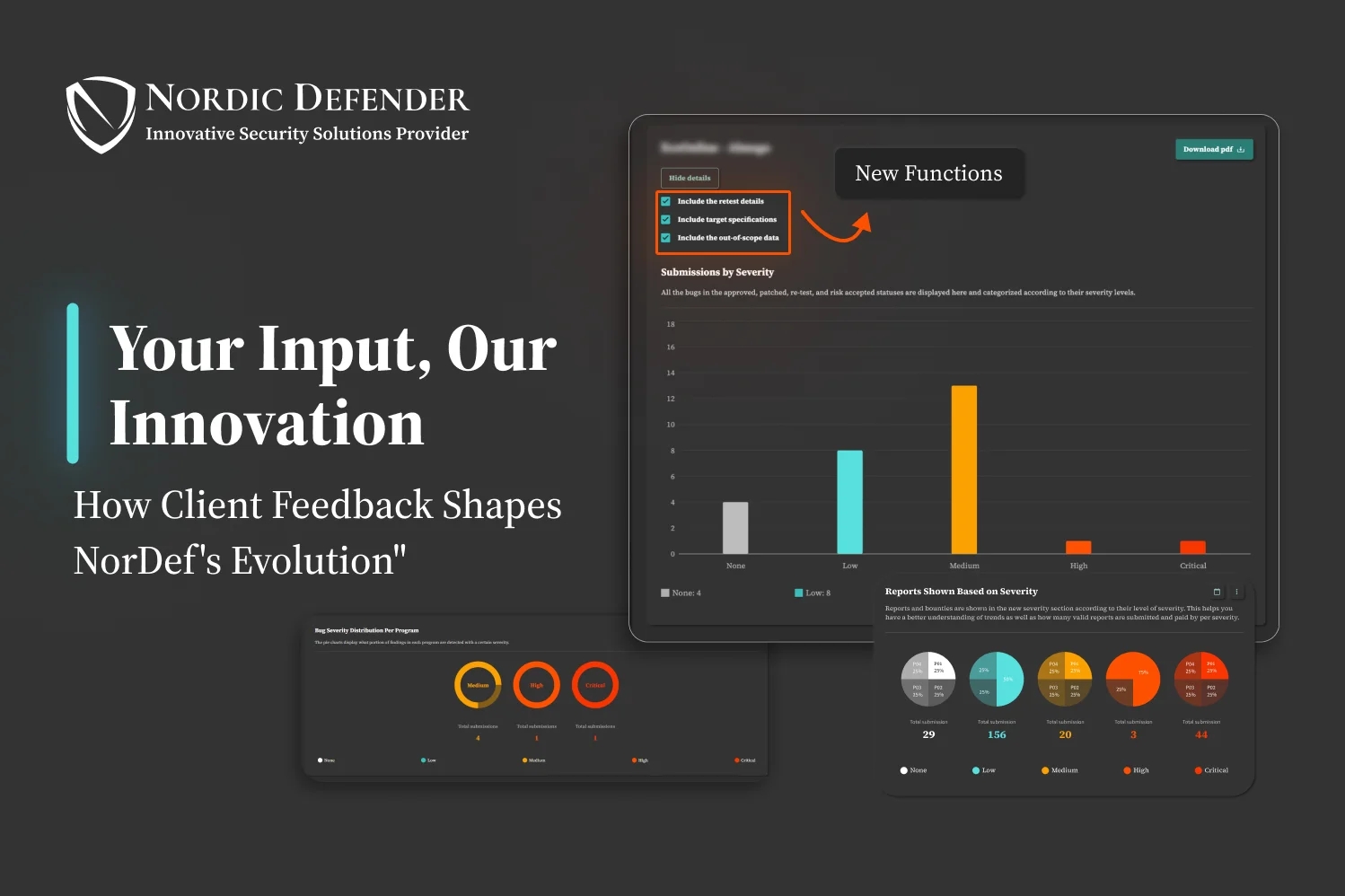
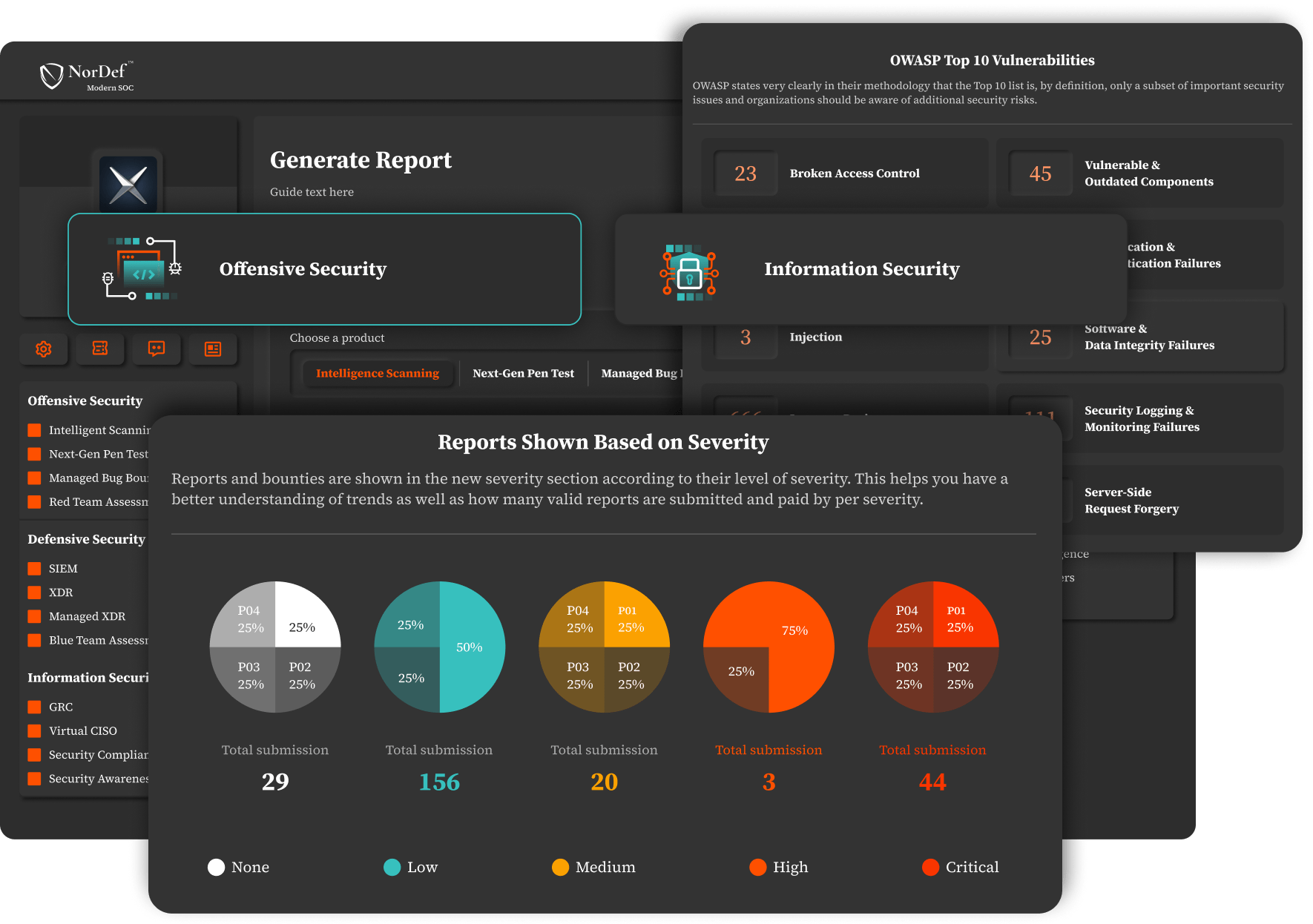
Get Clarified ReportsWith just a few clicks, get through reports on the total - and per program- number of security incidents found - vulnerabilities, bugs, and threats- with different categorizations based on severity, triage process, status count, OWASP Top 10, etc.
Powering Success: Safeguarding Industry Pioneers
Explore the impressive array of renowned brands that have chosen to partner with us. From global giants to innovative startups, our client roster reflects the unwavering trust they have in our solutions and services.

Ready to Proactively Secure Your Business?
Blog Post