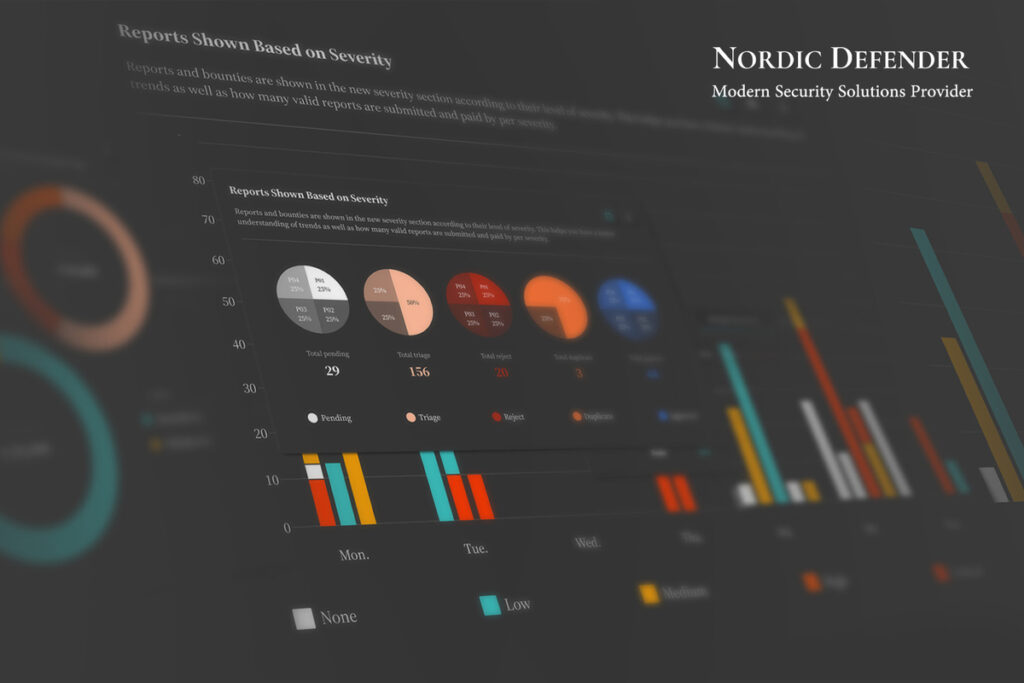
Patch Management vs. Vulnerability Management: Key Differences + Top Tools & Policy
The questions regarding ‘patch management vs. vulnerability management’ have become an essential part of cybersecurity discussions, especially with the relentless march of technology adding fuel to the flames of cyberattacks. When it comes to safeguarding sensitive data and critical systems, patch management and vulnerability management can spell the difference between a robust defense and a …
Patch Management vs. Vulnerability Management: Key Differences + Top Tools & Policy Read More »