In a landscape where cyber threats evolve rapidly, traditional compliance measures often struggle to keep pace with modern security demands. Compliance as a Code (CAC) offers a transformative solution, automating compliance through code to achieve higher accuracy, faster deployment, and proactive defense against vulnerabilities. This blog explores how CAC can streamline compliance, strengthen security, and prepare organizations for the future.
What is Compliance as a Code (CAC)?
Compliance as a Code (CAC) is the practice of embedding compliance requirements directly into code, creating automated checks and balances within digital infrastructures. By codifying policies, regulations, and best practices, CAC enables continuous monitoring and enforcement of compliance standards, from configuration management to data handling practices. Instead of relying on periodic manual audits, CAC integrates compliance into the development lifecycle, ensuring that standards are met automatically.
Key Benefits of Compliance as a Code
Automated and Consistent Compliance
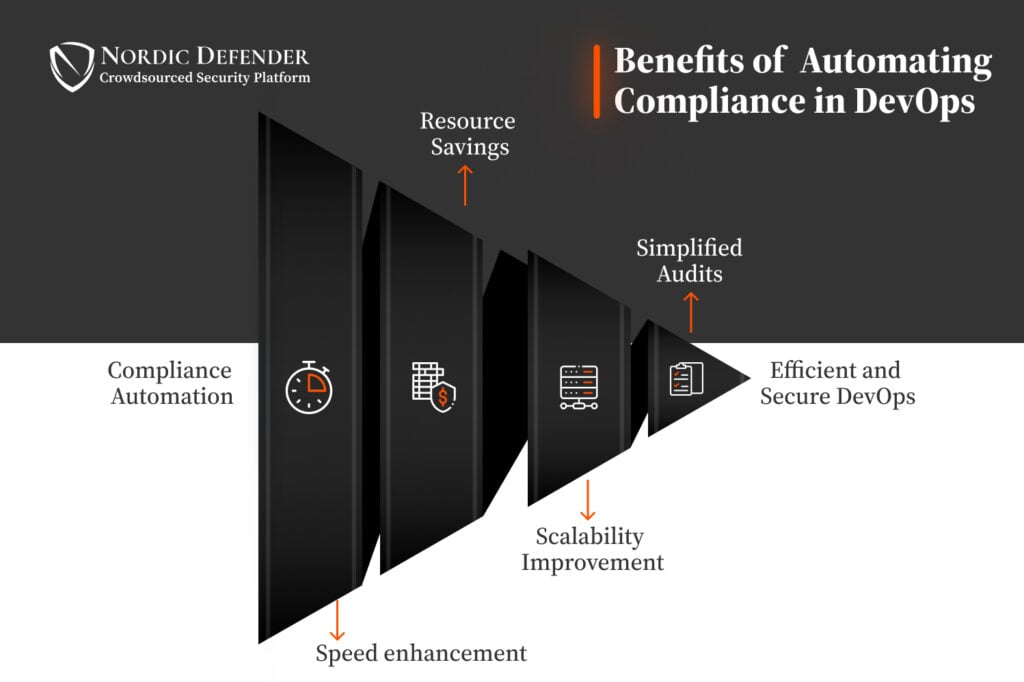
CAC allows organizations to automate repetitive compliance tasks, reducing human error and ensuring consistent adherence to policies. This is especially useful in dynamic cloud environments, where constant changes can create compliance drift. Automated checks instantly validate configurations and detect misalignments, keeping systems secure and aligned with regulatory requirements.
Enhanced Agility and Speed
Traditional compliance processes can be lengthy and disrupt workflows. With CAC, compliance becomes a part of the DevOps pipeline, accelerating product releases while maintaining regulatory standards. Teams can detect and correct issues early in development, speeding up time-to-market without compromising security or compliance integrity.
Proactive Risk Management
CAC offers real-time visibility into compliance status, helping organizations identify risks before they escalate. By defining rules and policies in code, companies gain the ability to monitor compliance continuously and address vulnerabilities before they become threats, a proactive shift from reactive security practices.
Implementing Compliance as a Code
Transitioning to CAC requires integrating compliance requirements within development workflows, especially in cloud-native and DevOps environments. Here are some essential steps:
Define Compliance Policies in Code
Identify critical regulatory standards—such as GDPR, HIPAA, or ISO/IEC 27001—and translate these into code-based policies. Use declarative languages to create templates or rules that specify how resources should be configured and monitored.
Utilize Infrastructure as Code (IaC)
CAC pairs effectively with Infrastructure as Code (IaC) tools like Terraform and AWS CloudFormation, which enable infrastructure configuration through code. By embedding compliance rules within IaC templates, organizations can ensure that each infrastructure deployment meets regulatory requirements automatically.
Integrate CAC into CI/CD Pipelines
Embed compliance checks into continuous integration/continuous deployment (CI/CD) pipelines. This enables automated testing and validation of each code change, ensuring compliance from development to deployment. Tools like Chef InSpec and Open Policy Agent (OPA) are excellent resources for integrating CAC with CI/CD workflows.
Automate Auditing and Reporting
Compliance audits are crucial, but manual checks can be labor-intensive and inconsistent. Automating auditing with CAC generates real-time reports, making it easier to track compliance and provide transparent documentation during regulatory reviews.
Tools and Technologies Supporting Compliance as a Code
A variety of tools can assist in implementing CAC by automating checks, scanning for vulnerabilities, and managing policies as code:
- Chef InSpec: A compliance-as-code framework that enables testing, reporting, and maintaining compliance.
- HashiCorp Sentinel: A policy-as-code framework integrated with HashiCorp products, allowing for flexible, codified policy management.
- Open Policy Agent (OPA): A general-purpose policy engine that works across cloud-native environments to enforce compliance policies.
- AWS Config: Monitors and records AWS resource configurations, evaluating them against CAC policies to detect non-compliant resources.
Best Practices for Effective CAC Implementation
Involve Compliance Teams Early
Collaboration between security, compliance, and development teams is crucial. By involving compliance officers from the outset, organizations can ensure that codified policies accurately reflect regulatory standards and organizational requirements.
Use Declarative Policy Language
Using a declarative approach to policy language helps simplify compliance code and makes policies easier to read, modify, and audit. Declarative languages express “what” the system should achieve, while procedural languages focus on “how” to achieve it.
Maintain Version Control of Compliance Code
Treat compliance policies as version-controlled code. This enables tracking of changes over time, audits of policy evolution, and quick rollbacks to previous versions if necessary.
Continuous Monitoring and Testing
Regular monitoring ensures that compliance standards adapt to changes in infrastructure and regulatory requirements. Use automated testing to continuously validate compliance and proactively address potential issues.
The Future of Compliance as a Code
The role of CAC is expected to expand as organizations adopt DevOps and cloud-native architectures at scale. By reducing reliance on manual audits and traditional compliance processes, CAC supports the transition to a security-first, agile infrastructure. Furthermore, with AI and machine learning enhancements on the horizon, CAC could evolve to offer predictive compliance capabilities, identifying potential risks before they materialize.
For organizations striving to stay secure and compliant in today’s complex regulatory environment, CAC represents a forward-thinking approach. Embracing Compliance as a Code not only strengthens security postures but also empowers teams to work more efficiently, meet evolving regulatory demands, and safeguard digital assets with confidence.
