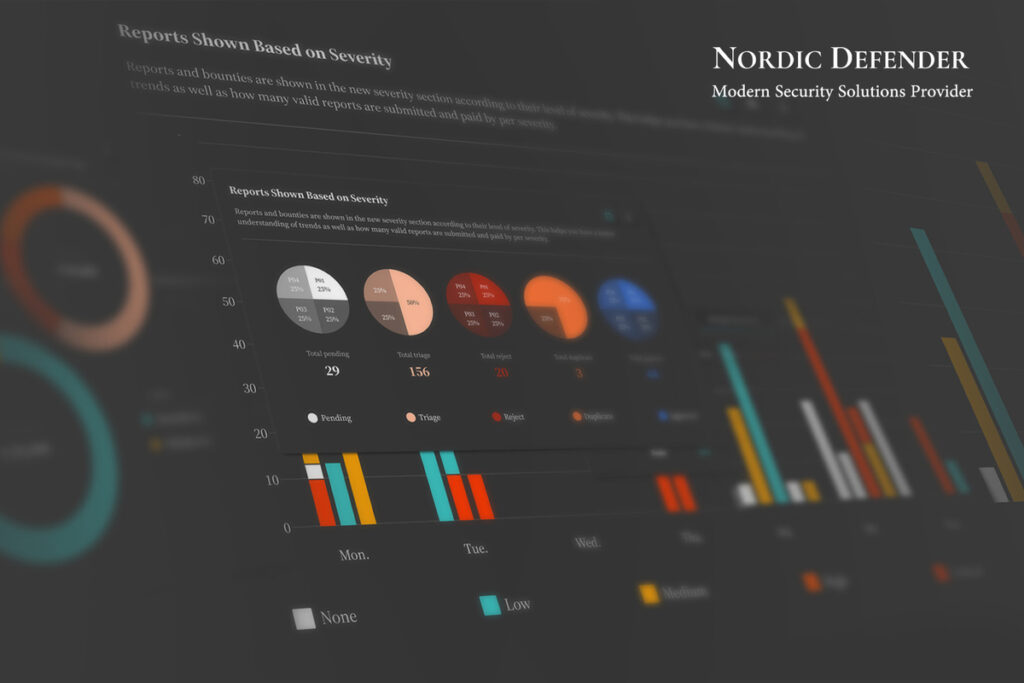
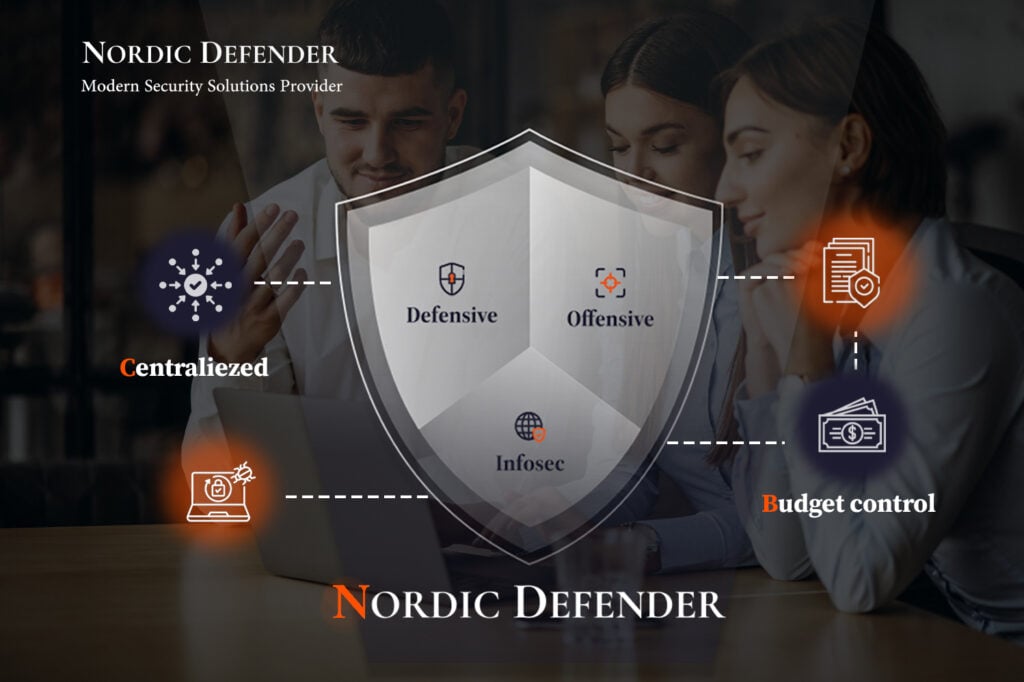
Cloud Network Security, Definition, Challenges, Benefits, Process, Controls & Best Practices
Cloud Network Security is a critical aspect of any organization’s security posture, particularly as more businesses move their operations and data to the cloud. It involves the implementation of security policies, procedures, and technologies to protect data, applications, and the associated infrastructure within cloud environments. Despite the challenges, effective Cloud Network Security can offer numerous …