In the world of cybersecurity, attackers are continually devising new techniques to exploit vulnerabilities and infiltrate computer systems. One such method gaining attention is the “System Binary Proxy Execution Rundll32” attack. This sophisticated attack leverages the legitimate Windows executable, rundll32.exe, in combination with specific dynamic-link libraries (DLLs) to execute malicious code or commands on the targeted system.
Understanding the Attack
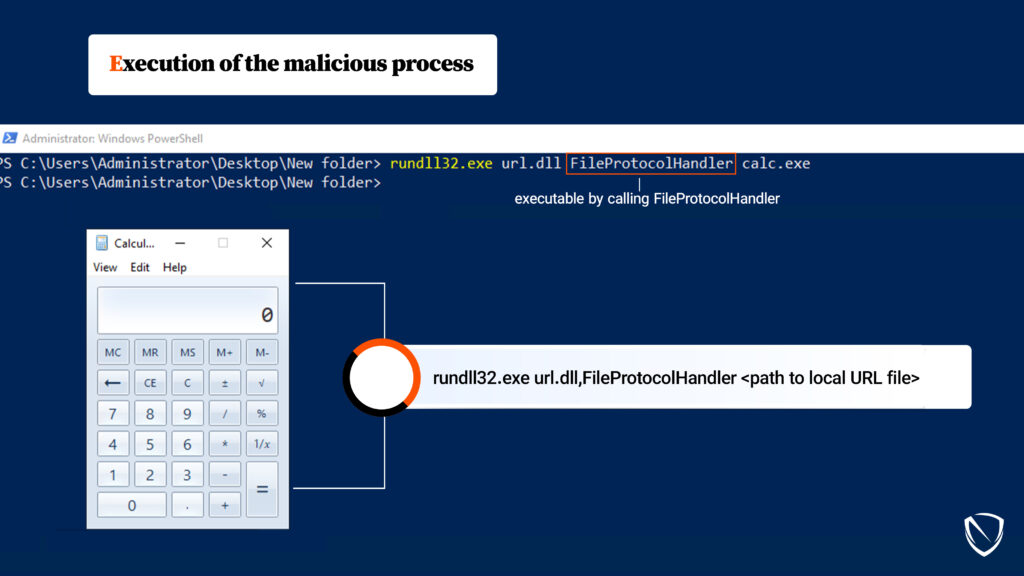
The described process involves loading an executable payload by using a .url file. A .url file is typically a harmless shortcut file used to store website links, but in this context, it is repurposed for malicious intent. The payload within the .url file is often a malicious program or script designed to perform unauthorized actions on a computer system. It’s important to note that this attack requires only user-level privileges, making it particularly insidious.
Operating System Compatibility
The System Binary Proxy Execution Rundll32 attack primarily targets Windows 10 and Windows 11 systems. Understanding how this attack works is crucial for defending against it.
MITRE ATT&CK® Framework
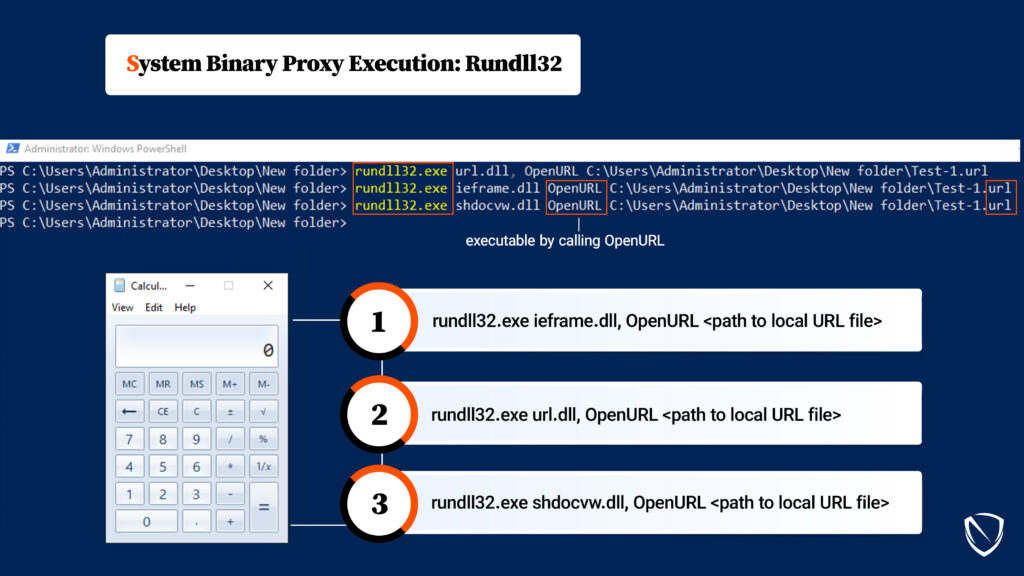
The MITRE ATT&CK® framework provides a comprehensive way to categorize and understand various tactics and techniques employed by threat actors. The System Binary Proxy Execution Rundll32 attack is cataloged under T1218.011.
The Role of Key DLLs: URL.dll, ieframe.dll, and shdocvw.dll
To comprehend the System Binary Proxy Execution Rundll32 attack fully, it’s essential to delve into the key DLLs involved:
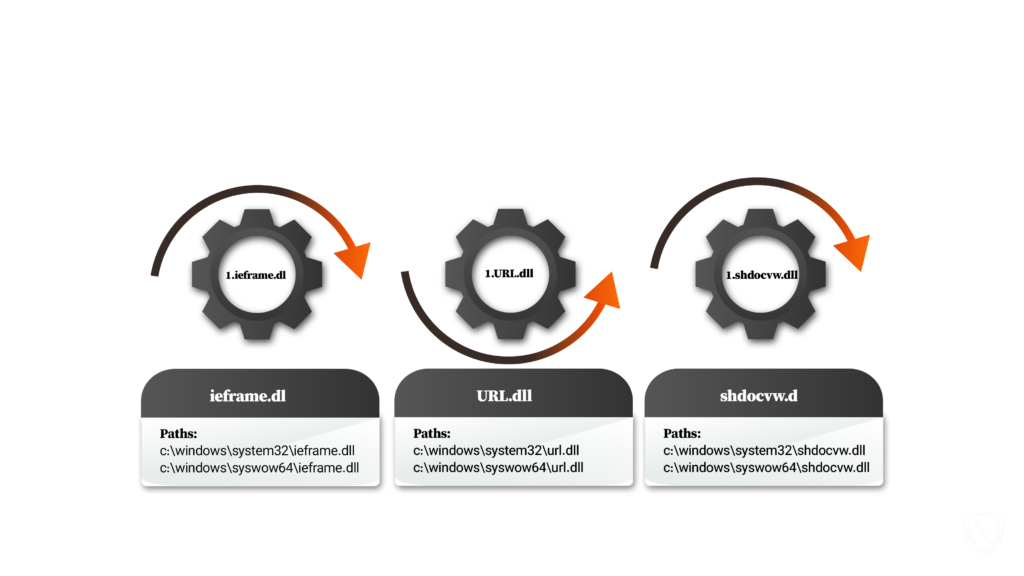
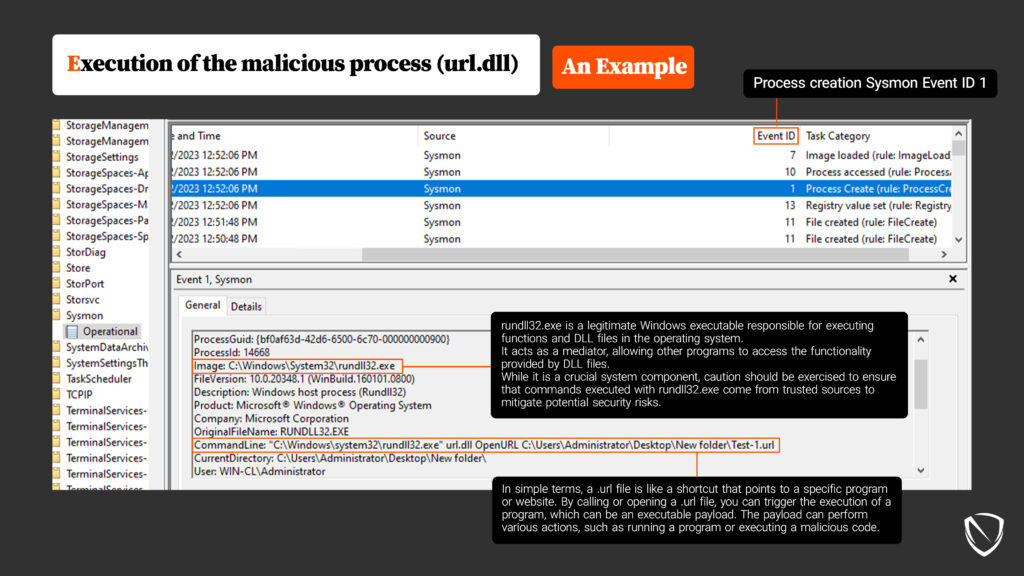
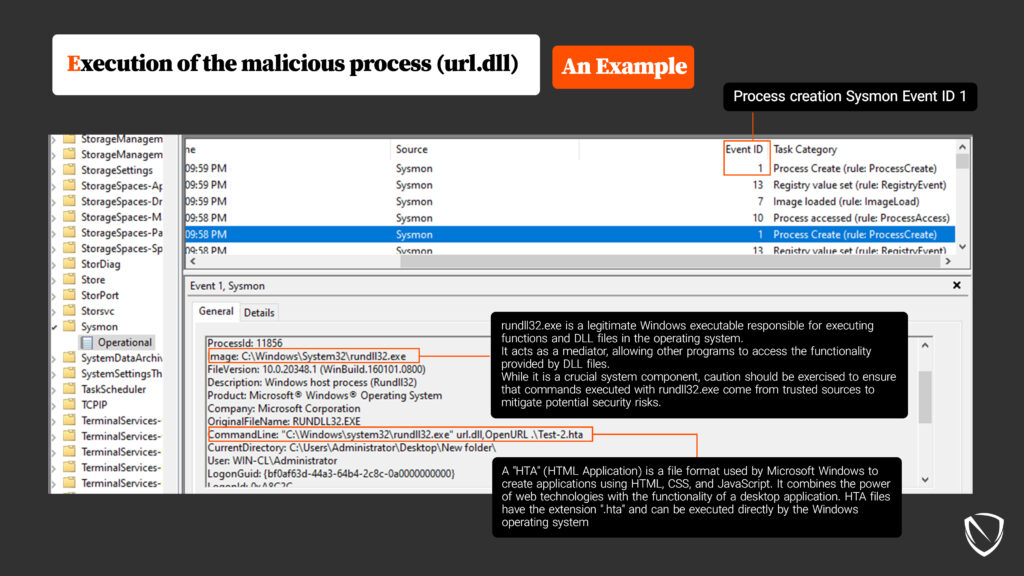
- URL.dll: This dynamic-link library, or DLL, handles Uniform Resource Locators (URLs). It is responsible for parsing and processing URLs, resolving relative URLs, and performing operations such as encoding and decoding URL strings. URL.dll is used by various applications, including web browsers like Internet Explorer. The paths to access it are:
- c:\windows\system32\url.dll
- c:\windows\syswow64\url.dll
- ieframe.dll: Internet Explorer Frame (ieframe.dll) contains functions and resources for rendering and managing the user interface elements of Internet Explorer. It provides the framework for displaying web pages, handling navigation, managing browser windows, and other related tasks. This DLL is an essential component of Internet Explorer. The paths to access this DLL file are:
- c:\windows\system32\ieframe.dll
- c:\windows\syswow64\ieframe.dll
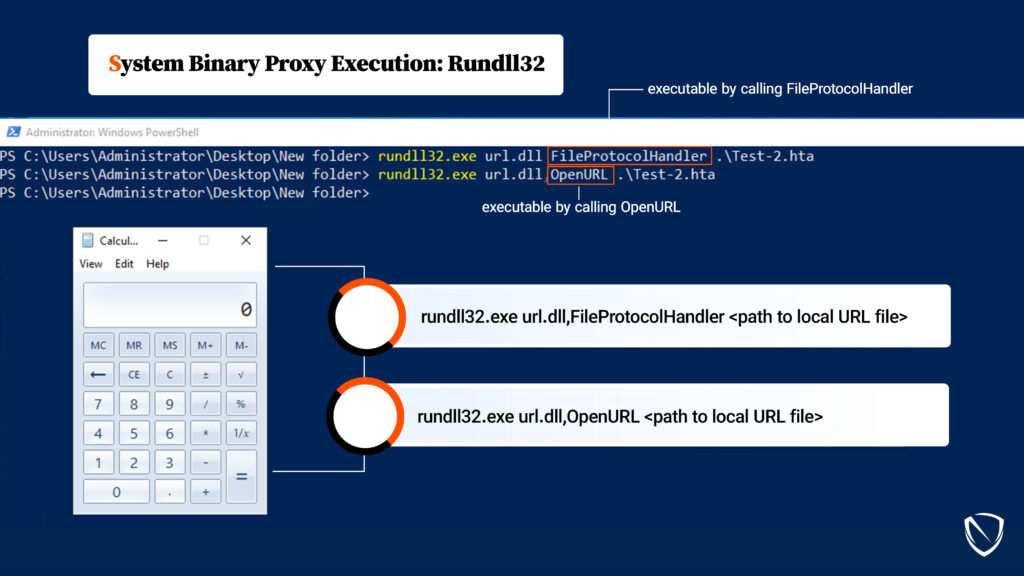
- shdocvw.dll: The Shell Doc Object and Control Library (shdocvw.dll) provides the programming interface for embedding web browser functionality into applications. It includes interfaces and classes for hosting the Internet Explorer web browser control, allowing developers to incorporate web browsing capabilities within their programs. The ieframe.OpenURL function mentioned is part of shdocvw.dll and is used to open a URL within the embedded browser control. The paths are:
- c:\windows\system32\shdocvw.dll
- c:\windows\syswow64\shdocvw.dll
Understanding URL Files
URL files are typically used to create shortcuts to websites or specific web pages. These files have a .url extension and are structured using a simple key-value format. Here’s a breakdown of the components of a URL file:
URL File Example
[InternetShortcut]
URL=https://www.example.com
IconIndex=0
HotKey=0
- [InternetShortcut] specifies that it is an internet shortcut file.
- URL represents the web address to which the shortcut points.
- IconIndex determines the index of the icon to be displayed for the shortcut.
- HotKey defines the keyboard shortcut to open the shortcut quickly.
When you double-click on a URL file, it opens the specified URL in your default web browser, redirecting you to the corresponding website.
How Attackers Exploit .url Files
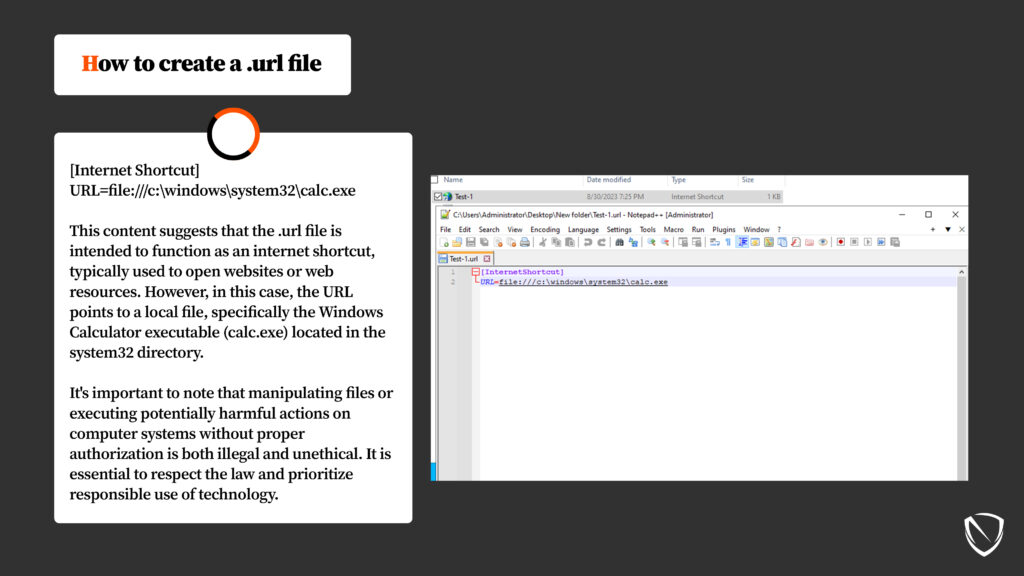
Attackers manipulate .url files to function as internet shortcuts, typically used to open websites or web resources. However, they point the URL to a local file, often a malicious executable, such as the Windows Calculator (calc.exe) in the system32 directory. It’s crucial to emphasize that manipulating files or executing potentially harmful actions on computer systems without proper authorization is both illegal and unethical.
HTA Files: A Powerful Weapon for Attackers
In the context of this attack, it’s essential to mention HTA (HTML Application) files. HTA is a file format used by Microsoft Windows to create applications using HTML, CSS, and JavaScript. HTA files have the extension .hta and can be executed directly by the Windows operating system.
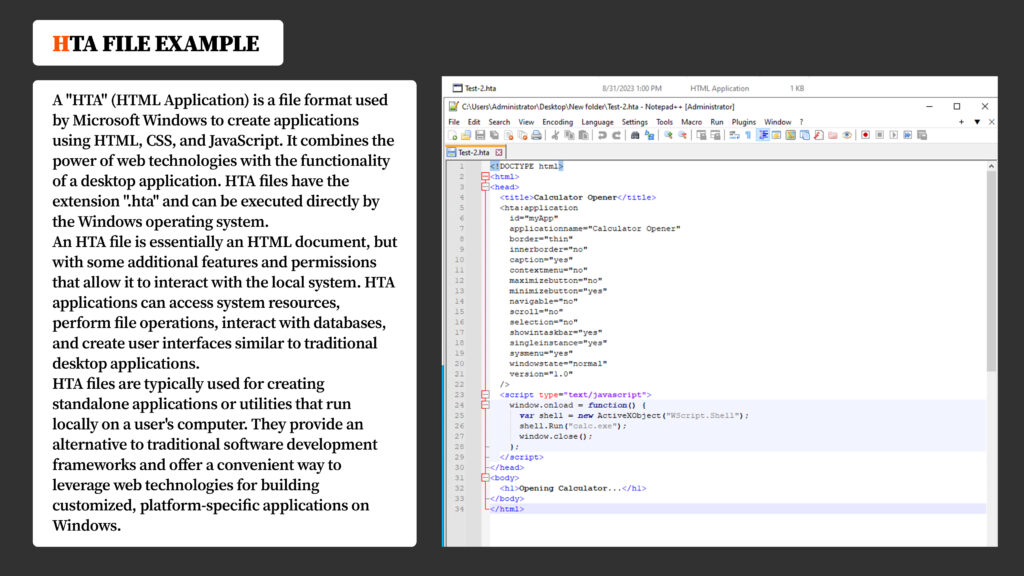
HTA files are essentially HTML documents with additional features and permissions that enable them to interact with the local system. They can access system resources, perform file operations, interact with databases, and create user interfaces similar to traditional desktop applications. Attackers often employ HTA files to further their malicious agendas.
Conclusion and Mitigation
The System Binary Proxy Execution Rundll32 attack highlights the cunning ways in which attackers exploit legitimate Windows features to compromise computer systems. By leveraging the rundll32.exe command along with DLL files like URL.dll, ieframe.dll, or shdocvw.dll, malicious actors can execute arbitrary code, perform unauthorized actions, and potentially gain unauthorized access to systems.
To mitigate the risks associated with this attack, it’s essential to:
- Keep your operating system and software up to date with the latest security patches.
- Use reliable security software to detect and prevent such attacks.
- Exercise caution when opening attachments or visiting unfamiliar websites.
- Follow best practices for online security and stay informed about potential vulnerabilities.
In an ever-evolving digital landscape, vigilance and a proactive approach to security are vital in safeguarding your systems against threats like the System Binary Proxy Execution Rundll32 attack.