In the ever-evolving world of cybersecurity, businesses face an increasing number of challenges to ensure the safety and integrity of their digital assets. Among these challenges is the intricate process of managing penetration test projects.
Penetration tests, although incredibly effective, can pose a few challenges in terms of skill matching, bug validation, risk assessment, and remediation management. The complexity of penetration test projects often proves to be a formidable hurdle for many organizations, especially those with few technical staff onboard.
In this blog, we will delve deep into what it means to manage a pen test project independently and how to avoid unnecessary complications.
The Complexity of Penetration Test Project Management
Penetration testing, a proactive approach to identifying and fixing security vulnerabilities, demands a comprehensive project management strategy. The multifaceted nature of penetration tests introduces various challenges that organizations must navigate:
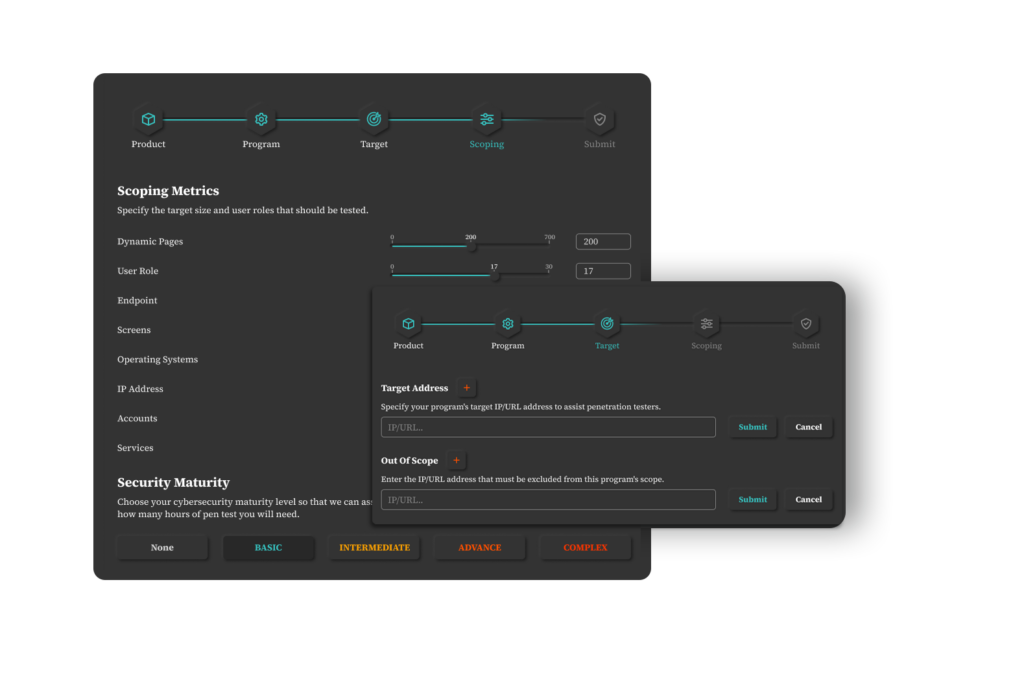
Scope Definition
Defining the scope of a penetration test is a delicate balance. Organizations must determine the depth and breadth of the assessment, considering the potential impact on operations and systems.
Clarifying what aspect of your infrastructure is open to inspection informs the testers about what’s off-limits and what they can thoroughly examine. Without a well-defined scope, the testing process may become unfocused and inefficient, potentially overlooking critical systems or failing to address specific security concerns.
This lack of clarity can lead to wasted resources, as penetration testers may spend valuable time exploring irrelevant areas, leaving essential systems and vulnerabilities unexamined and therefore vulnerable to cyber attacks. Additionally, the absence of a defined scope can result in misunderstandings between the organization and the testing team, leading to misaligned expectations and potentially exposing sensitive information unintentionally.
Diverse Testing Techniques
Penetration tests involve various techniques used for various scopes, ranging from network and applications to K8S and Scada testing. Coordinating these different approaches requires meticulous planning and execution, without which the penetration test fails to provide a comprehensive assessment of the organization’s security posture and leaves potential vulnerabilities unexplored.
Skill Matching
Building a pentest team involves identifying individuals with diverse skill sets, expertise in the type of pentest you’d like to run (Cloud, Kubernetes, Network, Web, etc.), and experience in your industry. To optimize the outcome of your pentest and ensure that it will bring you closer to your ideal security maturity, you should collaborate with pentesters whose expertise and experience align with your requirements.
Risk Assessment & Severity Prioritization
Identifying vulnerabilities is not enough; understanding their severity is crucial. Prioritizing vulnerabilities based on potential impact and exploitability demands a deep understanding of the threat landscape, the organization’s assets, and the potential consequences of exploitation.
Integration with Development Life Cycle
Ultimately, the penetration testing results boil down to valid vulnerabilities with assigned priorities, along with verified steps for remediation that need to be seamlessly incorporated into the development lifecycle and promptly addressed. Failing to integrate these findings into the life cycle can lead to delayed or ineffective fixes, potentially exposing the organization to data breaches and cyber attacks.
Effective Penetration Test Management
Amidst these challenges, organizations are increasingly turning to cybersecurity solutions to handle the complexities of penetration test project management. Here’s how NorDef has helped multiple organizations manage their penetration tests without the slightest hassle!
Technical Onboarding & Consult
During this process, you have NorDef’s technical consultants to walk you through it and help you accurately specify the scope of the project and lay down the ground rules.
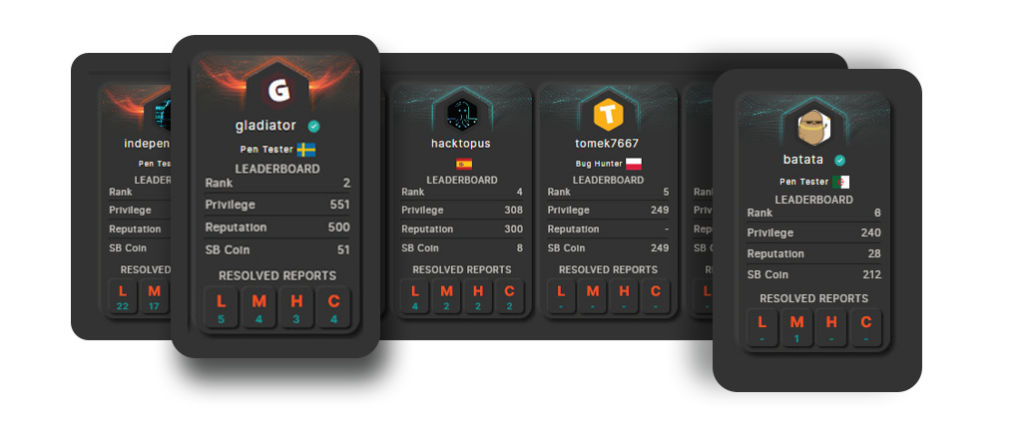
NorDef’s Advanced Skill Matching
With access to a crowd of penetration testers from the world over, the ethical hackers assigned to your project would be the perfect match for your type of pentest. NorDef’s highly vetted experts bring their expertise and specialization to the table, ensuring that your pre-defined scope is thoroughly inspected.
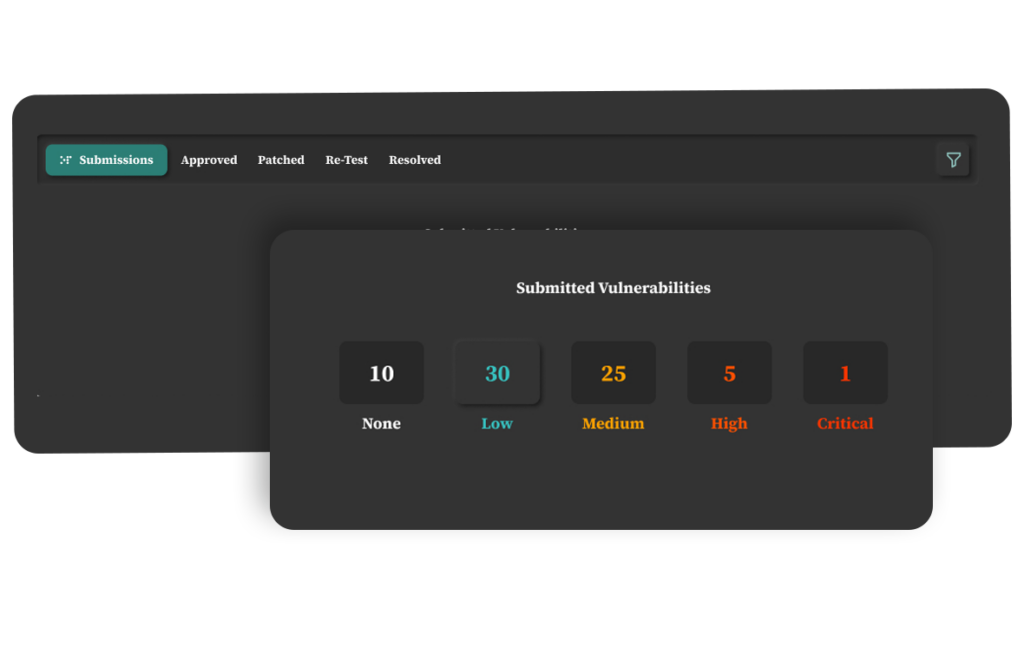
Comprehensive Bug Detection
No matter the type of penetration test you’d like to run, you can draw on the right skills and rely on the selected penetration testers to employ cutting-edge tools and methodologies to detect a wide range of vulnerabilities comprehensively. Their expertise allows for the identification of subtle and advanced security issues that may elude traditional testing methods.
Severity Assessment and Prioritization
The importance of accurately assessing the severity of vulnerabilities and validating them shouldn’t be taken lightly. This ensures that your most valuable resources are assigned to the most critical issues first, minimizing potential risks.
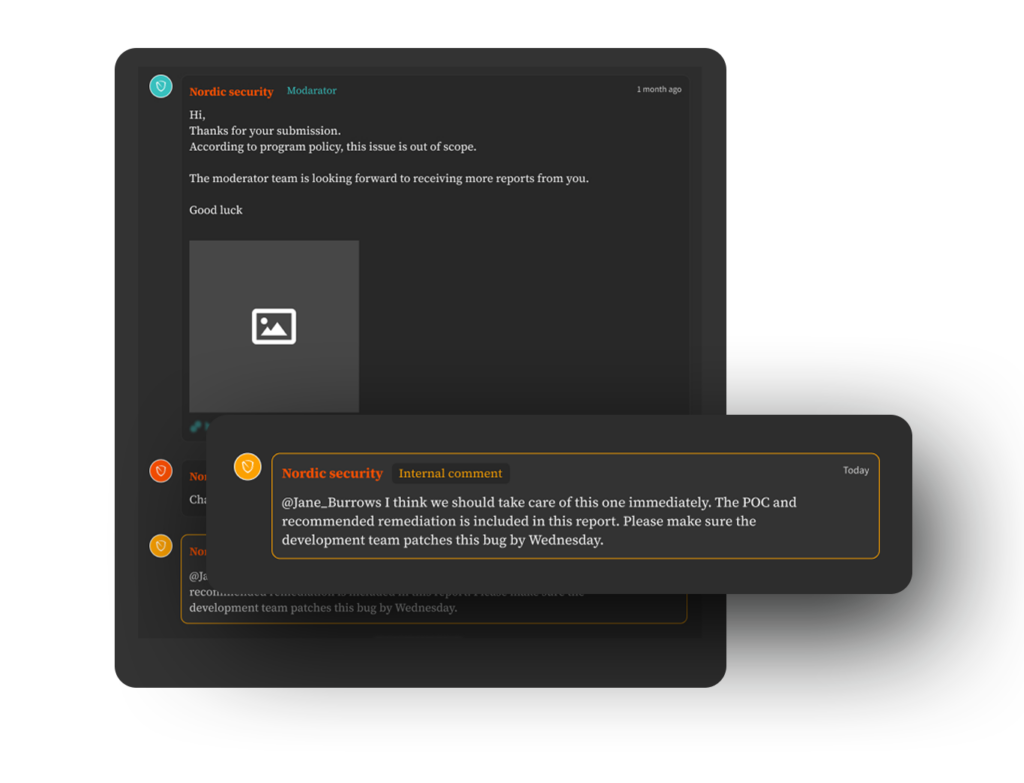
While in a traditional penetration test, you would need to rely on your own internal team to validate and assess the risks associated with a detected vulnerability, in NorDef’s Next-Gen pentesting approach, this responsibility is left to the experienced security experts, AKA moderators, to validate the bugs, prioritize them, and add complementary information to make sure your security team can start patching vulnerabilities without wasting a second.
Valid Remediation Strategies
Armed with extensive knowledge and experience, NorDef’s security experts go through the remediations provided by the testers to make sure that only valid and effective remediation strategies find their way into the report. Their insights go beyond mere identification, providing actionable steps to address vulnerabilities.
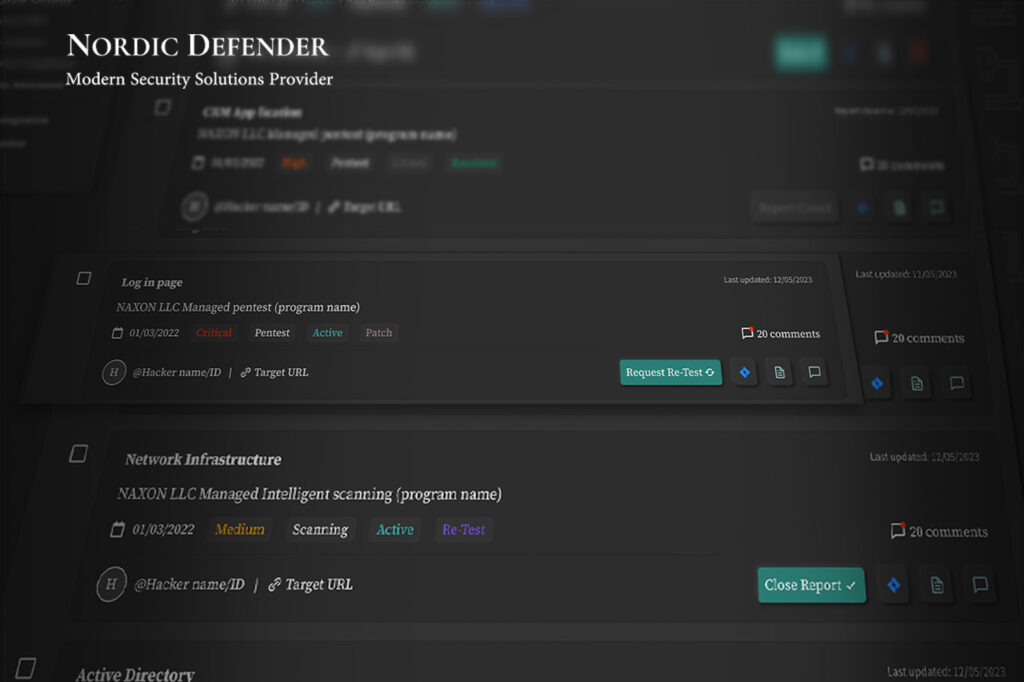
Real-Time Bug Reporting
Perhaps the most critical step to managing a penetration test is receiving the results in time. With the ability to take your team on board the platform and give them granular access permissions, you’re allowing your trusted employees to take the matter into their own hands, view the bugs as soon as they come in, watch the bug lifecycle as it goes through different stages of validation and moderation, and finally monitor the results or even download the reports to present to you and other stakeholders.
Direct Communication
Direct communication enables real-time collaboration between your security staff and the penetration testers and security experts assigned to your project. This fosters a more dynamic exchange of information, allowing for quick clarification of requirements, immediate feedback on findings, and prompt resolution of any queries that may arise during the remediation process.
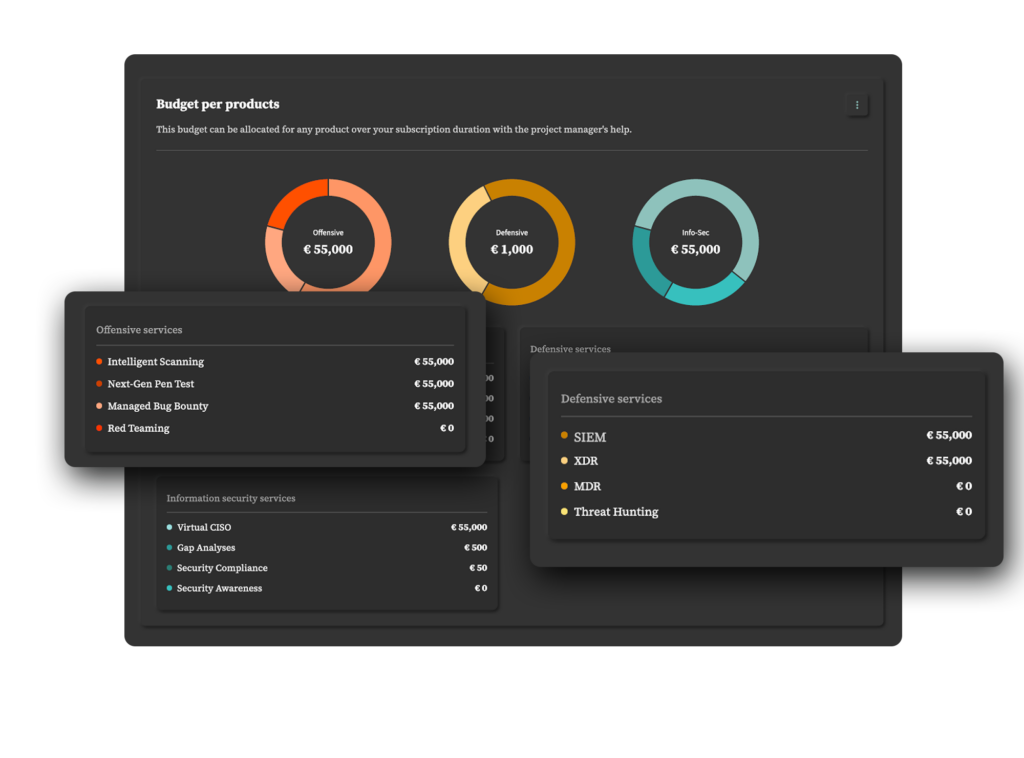
Budget Reporting & Monitoring
NorDef’s detailed budget reporting features a detailed breakdown of expenses, providing a clear overview of allocated resources to help the organization plan and control costs effectively. This way, you’ll make sure that no expense goes amiss.
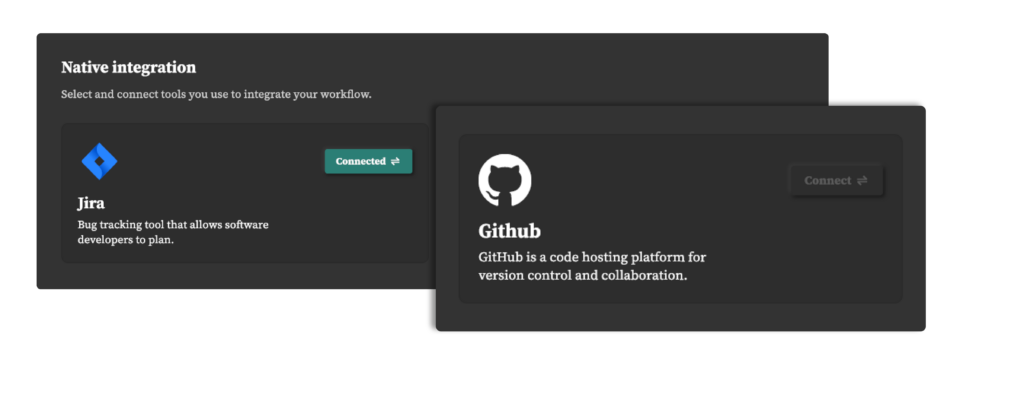
Integration into the Development Life Cycle
Successful penetration test project management doesn’t end with vulnerability identification. NorDef also assists organizations in seamlessly integrating remediation into the development life cycle, ensuring a more refined security posture.
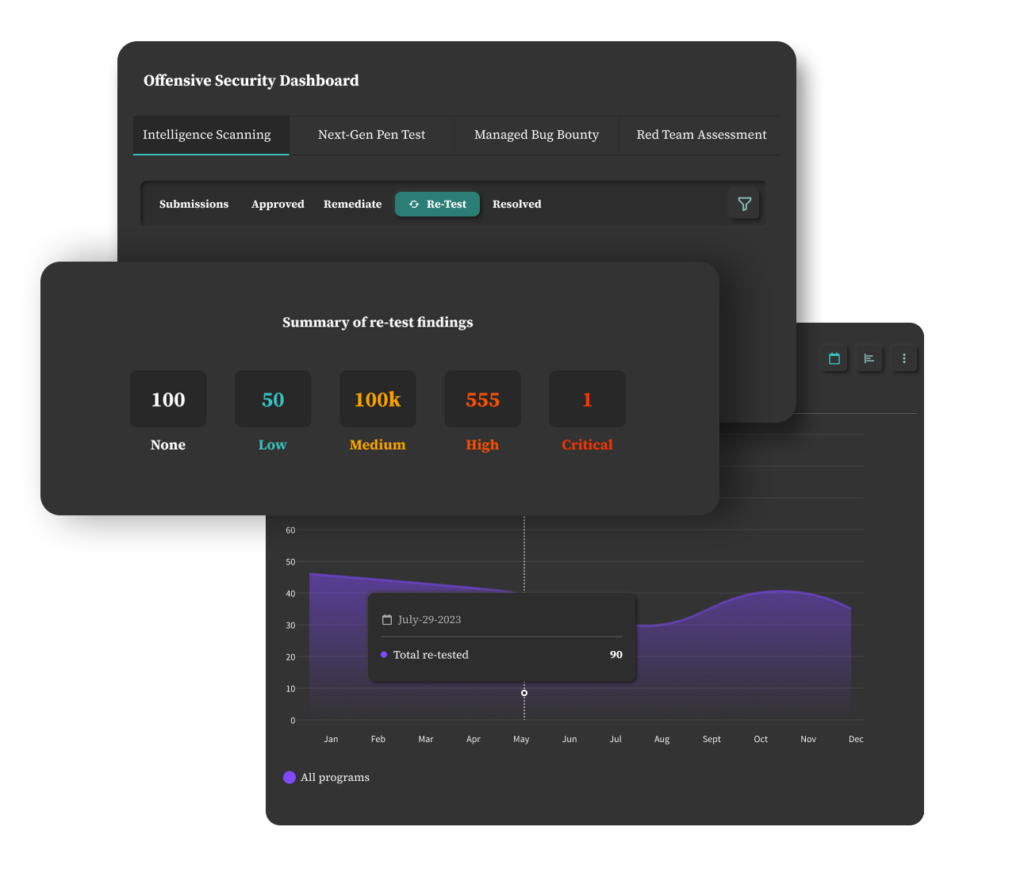
On-Demand Re-Testing
On-demand retesting serves as a validation mechanism for the effectiveness of remediation efforts. It ensures that the identified vulnerabilities have been successfully patched or mitigated, providing confidence that the security measures put in place are indeed addressing the identified risks.
Last Words on Pentest Project Management
In the intricate world of penetration test project management, Nordic Defender’s Next-Gen Pentest has emerged as a strategic move for many organizations. The complexities of scope definition, testing techniques, severity prioritization, and integration into the development life cycle require a level of expertise that NorDef is well-equipped to deliver. We have completed security projects, especially penetration testings, for over 40 satisfied clients. Read their success stories here. By entrusting the management of penetration test projects to specialists, organizations can fortify their defenses, detect vulnerabilities, and proactively mitigate potential risks in today’s dynamic cybersecurity landscape.