Have you been wondering what is bug bounty AKA vulnerability rewards program and how can it possibly help you fortify your security posture?!
In a world where technology is rapidly enhancing, different forms of cyberattacks are also appearing on the landscape, giving cybercriminals enough ammunition to wage war against the safety, privacy, and confidentiality of any company.
In this digital age, companies and businesses constantly find themselves exposed to data breaches and attacks. One of the most critical moments in the history of most failed businesses is when their security posture fell short and cybercriminals managed to penetrate their network. Losing confidential information or sensitive data can disrupt the activities of a business and damage them beyond repair.
To proactively protect their digital assets from falling prey to cybercriminals, organizations need modern cybersecurity solutions like bug bounty. After all, prevention is better than cure; especially in the field of cybersecurity where sometimes cure is not even an option!
So, in this blog, we’re going to answer questions on ‘what is bug bounty?’ and how benefits of bug bounty programs can work to your security advantage. Let’s start.
What Is Bug Bounty in Cyber Security?
In short, a bug bounty is a bounty, reward, or generally monetary compensation given to ethical hackers and security experts in exchange for the security vulnerabilities and bugs they detect in the cybersecurity posture of a company.
Security experts who identify unique, verified bugs of the severity levels specified by the company are qualified for the bounty! They might even receive public recognition alongside the reward. That’s why many white-hat hackers try bug bounty hunting as their main source of income or just to practice their skills in a safe environment.
Running a bug bounty especially appeals to organizations that are willing to offer rewards to independent security experts who will make every effort to find remaining vulnerabilities in a system or network.
What Is a Bug Bounty Program?
Now that we’re clear on ‘what is bug bounty hunting’, it’s time we learned about the programs and how they function.
A bug bounty program enables organizations to define a scope and call upon ethical hackers to find bugs in that scope and report back with fixes before bad actors can get their hands on these vulnerabilities and exploit them. The reward system will also be defined in the bug bounty policy; specifying the budget allocated to each security vulnerability of a certain severity.
Launching this program would allow companies to proactively protect their online assets against cyberattacks and data breaches. In effect, they’d be preventing attacks before they occur and take their toll on the company!
Bug bounty programs usually come in 2 variations: private and public. The former variation allows access to a small number of security experts to identify vulnerabilities. On the other hand, in the latter variation, your project will be open to all the ethical hackers in the community, and they will start performing tests on your assets to arrive at bugs and their solutions.
Based on your security requirements and priorities, you can decide on the type of program you’re going to need!
What Is the Difference Between Pentest & Bug Bounty?
Understanding ‘what is bug bounty’, you must have realized that bug bounty programs are different from penetration tests. In a crowd-sourced pentest, a few selected ethical hackers will be in charge of inspecting your cybersecurity posture to help you conform to various compliance. So, the primary objective is usually fixing vulnerabilities to acquire certain compliance.
However, in bug bounties, security experts can look into any aspect of a defined scope and inform you about your security vulnerabilities regardless of compliance requirements.
Not to mention that in a bug bounty, you’ll have the option to open doors to the community of ethical hackers or start with a limited 20-person group and increase the number as you go along. However, in a penetration test, your project will be assigned to a group of 4,5 individuals who are highly experienced in a specific field of work.
To delve deeper into how bug bounties may differ from crowd-sourced or even traditional pentest, you can check out our blog on pentest vs bug bounty.
What Is the Difference Between VDP & Bug Bounty?
Another yet important distinction we need to make is between a bug bounty and a VDP. A vulnerability disclosure program is basically a framework that allows companies to open their doors to independent security researchers and inform them about how they can submit bug reports. To show appreciation and gratitude, companies can offer gifts or monetary compensation.
This would mean that in a VDP, there’s no sign of inviting security experts based on skills or rewards allocated to each vulnerability!
How to Choose a Bug Bounty Program
Among all different Bug Bounty platforms, you need to choose the one that aligns with your security requirements and also matches your country’s regulations. So, the first factor to consider is to make sure the solution you’re running allows:
- enough flexibility for you to start/pause the program at will,
- optimize the rewards or program policy as you proceed,
- perfect alignment with your development lifecycle,
- adjustable pricing that doesn’t go beyond your cybersecurity budget,
While ensuring that your information won’t be exposed!
Nordic Defender, as the first and only bug bounty solution provider in the Nordics, offers one of the most flexible and efficient bug bounty programs! With the help of Nordic Defender, companies can have more than 7000 talented ethical hackers test a scope of their cybersecurity posture and come up with bugs that need to be fixed. The zero-commission policy on Nordic Defender also makes sure that hackers are motivated enough to dig deeper!
Whether you run a private or public bug bounty, Nordic Defender allows you to start several bug bounties on different scopes at the same time. Plus, the fully-managed bug bounty plan would allow you to leave drawing up your bug bounty policy and rules to the technical account managers!
Yet perhaps one of the best features provided by Nordic Defender is the validation process that each security vulnerability will go through before they reach you. Nordic Defender’s team of mediators are in charge of checking the validity and severity of each submitted bug to make sure that the report you get contains only the verified vulnerabilities and fixes!
If you have any questions about Nordic Defender’s bug bounty, make sure to contact the experts!

What Is the Purpose of a Bug Bounty?
Did you know that in May 2023, Open AI’s Chat GPT confirmed a data breach in the system?! Despite Open AI’s power and strong claims of security and safety, it wasn’t able to stop attacks from happening, and the data breach, even though it was only surface-level, managed to take Chat GPT offline for a short while.
In this landscape where even the most seemingly formidable companies are at risk of cyberattacks, every business should consider proactive safeguards to protect their online assets. One of the best solutions in this respect is bug bounty!
Essentially, bug bounty programs are developed to help foster a safer, more secure cyber world through advanced bug finding. Leaving the task of identifying security vulnerabilities to a pool of security experts means that your defined scope will receive enough attention, and you will finally arrive at a more robust security posture.
Now that we’re familiar with ‘what is bug bounty?’, it’s time we delved deeper into the purpose and benefits of this program.
Bug Bounty Helps Find Remaining Vulnerabilities
Although crowd-sourced pentests can help any company find their vulnerabilities, especially when it comes to acquiring compliance, many security bugs and flaws can go unnoticed. In this situation, identifying the remaining vulnerabilities through penetration tests becomes quite a challenge.
That’s when bug bounty comes to play! With a strong crowd of talented security experts behind the solution, a bug bounty program ensures that all remaining vulnerabilities and security bugs are detected. So, you can be sure that you’ll come out of the program a more secure company!
Bug Bounty Programs Come with Updated Reports
Nordic Defender’s Next-Gen Pentest as well as Bug Bounty program update the vulnerability reports as soon as bugs are verified by the moderators, which means that you will have access to constantly updated reports from your security vulnerabilities and fixes that you can immediately share with your development team.
Running Bug Bounty Builds Credibility
As a result of fixing your remaining vulnerabilities according to the reports you will receive during a bug bounty program, your security posture will be more robust and resilient against attacks and data breaches. Consequently, your attention to cyber security and proactively protecting your client’s data will earn credibility and reputation for your company!
How Does Bug Bounty Work?
You already know what is bug bounty. Now, let’s consider how bug bounty works. While the function of a bug bounty solution and the concept of a bug bounty are shared by many solution providers, each program can offer its own distinguishing procedure. In a centralized solution like Nordic Defender, the process is extremely straightforward.
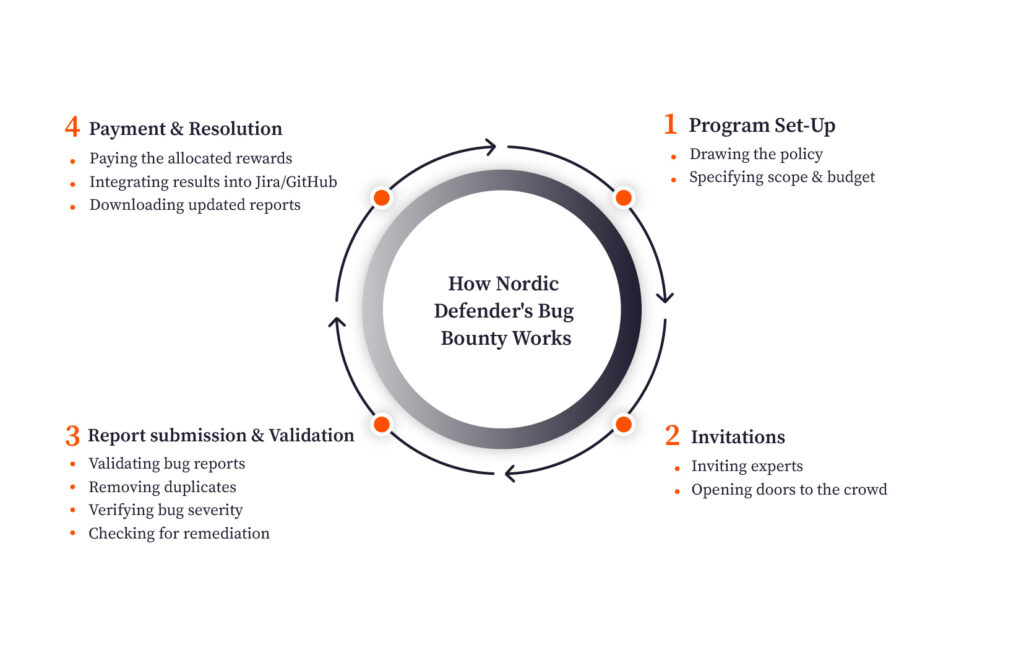
Step 1- Setting Up Bug Bounty Program Policy, Scope, & Budget
In the first step of Nordic Defender’s Bug Bounty program, the technical team will schedule a meeting with you to discuss your concerns, needs, and conditions. During this session, you can define the scope of the bug bounty, the program policy and rules, and the reward you would like to attribute to each vulnerability. Every step of the process will be clarified and tailored to your specific needs.
Perhaps the best part about this program is that the technical account managers accompany you step by step to make sure everything falls into its place to bring about a highly efficient bug bounty.
Step 2- Inviting Experts or Opening the Doors to the Public
After defining the rules, scope, and budget, it’s time to run the program. At this stage, you need to choose whether you’re comfortable with a private or a public bug bounty program. In case you choose the private edition, bug hunters will be chosen based on their expertise and background and assigned to your project. And if you choose the public program, all the bug hunters in the crowd can see the requirements and get down to work.
Remember that many companies would rather start with the more conservative approach of a private bug bounty, and later switch to the public mode as their security posture gains more maturity.
Step 3- Validating Vulnerabilities & Their Urgency
After inviting the right skills to come onboard, reports will start coming in. At this stage, Nordic Defender’s team of expert moderators will go through the reports, validating the quality of bugs, their severity, as well as the provided solutions. They will also make sure that duplicate bugs and vulnerabilities are removed from the results. Once they’re done with this verification process, you will receive the vulnerabilities that are labeled according to their severity.
Step 4- Paying the Reward & Resolving the Issues.
If the bug hunters have found vulnerabilities in the defined scope and with the specified severity, you can now pay the reward you had promised in the first place. Then, you can inform your development team about the identified bugs and how they can be resolved. This step becomes extremely easy on Nordic Defender as there’s an integration with Jira and GitHub.
If you’re ready to launch your bug bounty program or if you’d like to learn more, schedule a meeting with the experts now!
Is Bug Bounty Ideal for All Companies?
According to what is bug bounty, you know that it is, in effect, a simulated attack on your digital assets to help you find the remaining security bugs, and therefore, not ideal for all companies! In fact, if businesses that have never tested their security posture before launch a bug bounty program, they will be unfortunately overwhelmed by the expenses as well as the number of critical bugs that are found and should be immediately fixed.
This means that bug bounty programs are only suitable for companies that have gone through regular penetration tests, inspected their digital assets for vulnerabilities, and arrived at a relatively robust security posture!
FAQs on What Is Bug Bounty
In this blog, we have fully covered bug bounty meaning and what bug bounty programs can do for your business. Now, let’s answer some frequently asked questions.
1- What Is the Basic of Bug Bounty?
Vulnerability rewards program(VRP) or a bug bounty solution is a method for finding security bugs through the help of ethical hackers. Once the companies define the scope and property on which they’d like to find vulnerabilities and specify the rewards, hackers will start coming in to detect bugs and patches.
2- Which Type of Hackers Are Involved in Bug Bounties?
A bug bounty is a solution to reward ethical hackers to identify vulnerabilities. That is, only ethical hackers or white-hat hackers are involved in the process, and cyber criminals or black-hats have no place in a bug bounty program!
To make sure the crowd of security experts who will test your security posture are all ethical hackers and no malicious actor can enter the pool of experts, platforms like Nordic Defender have vetting processes. During this process, Nordic Defender will verify the hacker’s passport, ID or driver’s license, address, social media, and every other essential information required to ensure they are not bad actors.
3- How Many Types of Bug Bounties Are There?
As discussed earlier, bug bounties come in 2 different modes of private and public. In a private bug bounty program, 20 to hundreds of hackers will be on the task of finding your security vulnerabilities. In a public bug bounty, however, the whole crowd of ethical hackers are invited onboard to check your security posture!
What Is Bug Bounty Wrapped-Up
Bug bounty programs are the perfect opportunity for companies to call upon hackers to detect all the vulnerabilities that have flown under the radar despite other cybersecurity measures! This solution serves as a win-win situation for both the hackers and the organizations because after the bug bounty, security experts will receive their rewards and companies will understand their vulnerabilities and how they can fix them.
If you’re interested in launching your own bug bounty or have any questions, contact our team of security experts; they can help you find the most efficient solution for improving your present cyber security status.
